So im currently studying for my Advanced Diploma of Network Security after completing my Diploma of Network Engineering about 12months ago. As part of my course I will be studying CEH, however I’ve decided to get a jump on things by integrating security into all my other subjects. I pulled out the long neglected EEEPC 701 that I was given as part of finishing my NE course and work on CCNA Security and CCNA Wireless.
Heres a pretty simple guide to getting the 701 up and running with a persistent Backtrack 3 on usb, fingerprinting with Kismet and cracking WEP with wesside-ng.
Firstly I followed the persistent usb details outlined at:
- http://forums.remote-exploit.org/tutorials-guides/14486-bt3-usb-persistent-changes-using-linux.html
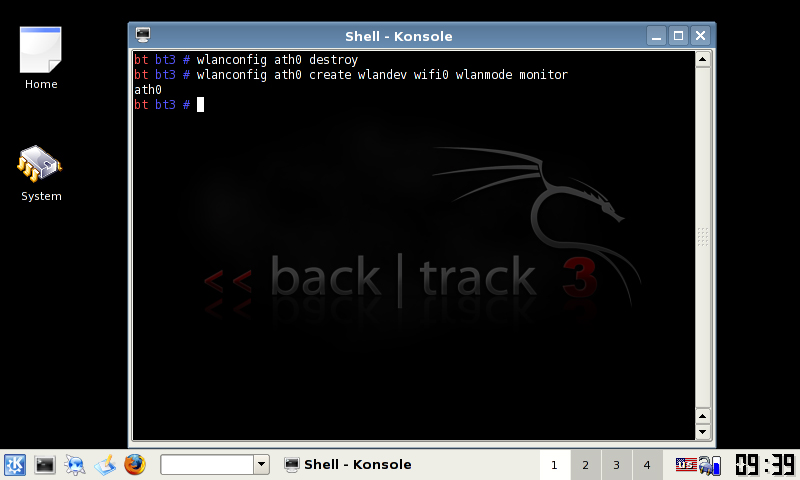
Secondly for each time you want to inject packets or use kismet run the following:
wlanconfig ath0 destroy wlanconfig ath0 create wlandev wifi0 wlanmode monitor
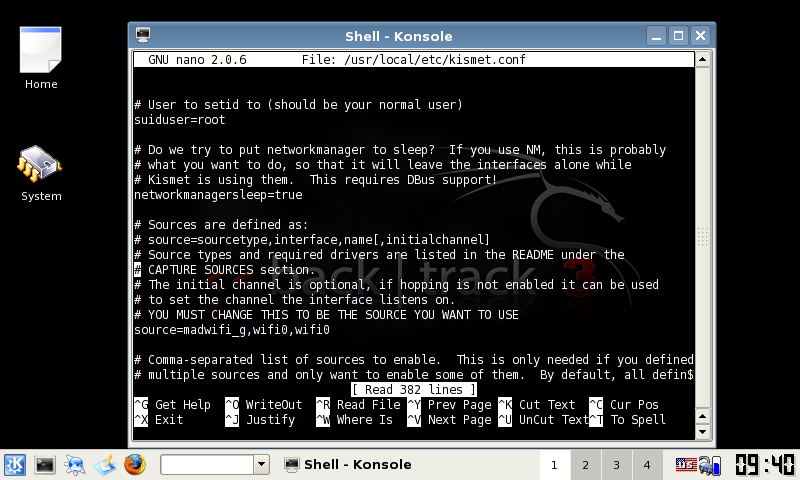
To run kismet, you will have to modify the following file. If you’re running BT3 live without persistence you will have to do this every time.
Edit /usr/local/etc/kismet.conf and change source to:
source=madwifi_g,wifi0,wifi0
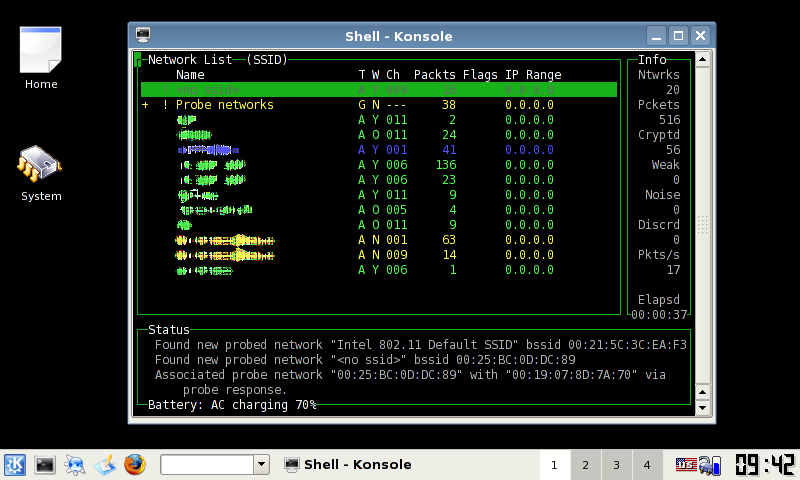
Finally, I wont record another WEP video like every other person on the net – just run the following to find the bssid mac of the AP (from kismet):
wesside -i ath0 -v MAC
Next I plan on running easside-ng for those networks where something doesn’t go right (occasional). Ill throw the details up for that when I’ve done it.